Another CTF writeup. Kudos to my team @ByteForc3 for finishing @ #6.
Jarred-1
Given a System map file ,a dwarf file and the ultimate VM. A classic package of Volatality challenge :).
Well it was a lubuntu image and zipping the dwarf and map file gave us the profile we needed for Lubuntu (as per in Volatality wiki :P). So the first thing i checked was the bash history with linux_bash plugin.
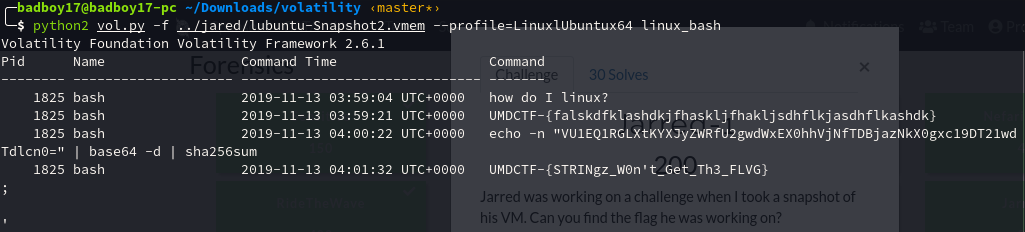
And there it was .
╭─badboy17@badboy17-pc ~
╰─$ echo -n "VU1EQ1RGLXtKYXJyZWRfU2gwdWxEX0hhVjNfTDBjazNkX0gxc19DT21wdTdlcn0=" | base64 -d
UMDCTF-{Jarred_Sh0ulD_HaV3_L0ck3d_H1s_COmpu7er}
Ezpz….
Jarred-3
This was another voltality chall with windows 7 image. This chall also had some ref to malware in the description. So looking at the process pstree gave us pretty image of what process were running and under whom .
╭─badboy17@badboy17-pc ~/Downloads/jared
╰─$ vol.py --plugins=volatility-plugins/ -f Windows\ 7\ x64\ -\ Jarred-Snapshot1.vmem --profile=Win7SP0x64 pstree
Volatility Foundation Volatility Framework 2.6.1
Name Pid PPid Thds Hnds Time
-------------------------------------------------- ------ ------ ------ ------ ----
0xfffffa800418b060:firefox.exe 2228 3204 49 749 2020-04-09 19:23:42 UTC+0000
. 0xfffffa80040f47e0:firefox.exe 3456 2228 10 196 2020-04-09 19:23:44 UTC+0000
. 0xfffffa800417b060:firefox.exe 3656 2228 21 320 2020-04-09 19:23:45 UTC+0000
. 0xfffffa8003860060:tor.exe 3668 2228 5 71 2020-04-09 19:23:44 UTC+0000
. 0xfffffa8002f9f240:firefox.exe 3992 2228 22 301 2020-04-09 19:25:02 UTC+0000
. 0xfffffa8004128630:firefox.exe 2328 2228 26 349 2020-04-09 19:23:45 UTC+0000
0xfffffa8003475b30:wininit.exe 412 332 3 76 2020-04-09 19:10:16 UTC+0000
. 0xfffffa8002919530:services.exe 520 412 6 204 2020-04-09 19:10:16 UTC+0000
.. 0xfffffa8003a98b30:VGAuthService. 1580 520 3 87 2020-04-09 19:10:18 UTC+0000
.. 0xfffffa80040bf310:svchost.exe 2704 520 15 161 2020-04-09 19:12:19 UTC+0000
.. 0xfffffa8003799910:svchost.exe 644 520 12 372 2020-04-09 19:10:17 UTC+0000
... 0xfffffa80063e1b30:WmiPrvSE.exe 1740 644 10 216 2020-04-09 19:10:19 UTC+0000
.. 0xfffffa8003eac890:dllhost.exe 2068 520 13 207 2020-04-09 19:10:20 UTC+0000
.. 0xfffffa8003f51300:svchost.exe 1648 520 13 324 2020-04-09 19:12:19 UTC+0000
.. 0xfffffa800393ba30:spoolsv.exe 1060 520 12 271 2020-04-09 19:10:17 UTC+0000
.. 0xfffffa80039a6b30:taskhost.exe 1192 520 8 155 2020-04-09 19:10:17 UTC+0000
.. 0xfffffa80037f5b30:svchost.exe 812 520 21 476 2020-04-09 19:10:17 UTC+0000
... 0xfffffa800386b060:audiodg.exe 964 812 6 132 2020-04-09 19:10:17 UTC+0000
.. 0xfffffa8004232060:sppsvc.exe 1732 520 4 149 2020-04-09 19:12:19 UTC+0000
.. 0xfffffa800396fa30:svchost.exe 1088 520 19 330 2020-04-09 19:10:17 UTC+0000
.. 0xfffffa80037c9b30:svchost.exe 724 520 8 295 2020-04-09 19:10:17 UTC+0000
.. 0xfffffa80038de060:svchost.exe 600 520 18 489 2020-04-09 19:10:17 UTC+0000
.. 0xfffffa8003cb0b30:vmtoolsd.exe 1684 520 12 276 2020-04-09 19:10:18 UTC+0000
.. 0xfffffa8003996b30:SearchIndexer. 2536 520 14 719 2020-04-09 19:10:24 UTC+0000
... 0xfffffa80016226c0:SearchFilterHo 2560 2536 5 100 2020-04-09 19:25:35 UTC+0000
... 0xfffffa8003f5ab30:SearchProtocol 2680 2536 8 449 2020-04-09 19:10:24 UTC+0000
.. 0xfffffa8003eb4b30:msdtc.exe 2156 520 12 148 2020-04-09 19:10:20 UTC+0000
.. 0xfffffa8003840b30:svchost.exe 884 520 42 1023 2020-04-09 19:10:17 UTC+0000
.. 0xfffffa8003810b30:svchost.exe 852 520 13 318 2020-04-09 19:10:17 UTC+0000
... 0xfffffa80039d84c0:dwm.exe 1260 852 3 74 2020-04-09 19:10:18 UTC+0000
.. 0xfffffa8003851b30:svchost.exe 1020 520 9 537 2020-04-09 19:10:17 UTC+0000
. 0xfffffa8005a933e0:lsass.exe 536 412 7 637 2020-04-09 19:10:16 UTC+0000
. 0xfffffa8002f977c0:lsm.exe 544 412 10 148 2020-04-09 19:10:16 UTC+0000
0xfffffa80072ae270:csrss.exe 368 332 10 433 2020-04-09 19:10:16 UTC+0000
0xfffffa8001423890:System 4 0 90 522 2020-04-09 19:10:10 UTC+0000
. 0xfffffa80032bcb30:smss.exe 276 4 2 30 2020-04-09 19:10:10 UTC+0000
0xfffffa80039fc870:explorer.exe 1284 1232 30 742 2020-04-09 19:10:18 UTC+0000
. 0xfffffa8003c903e0:vm3dservice.ex 1560 1284 2 46 2020-04-09 19:10:18 UTC+0000
. 0xfffffa8003c9cb30:iexplore.exe 1596 1284 18 709 2020-04-09 19:10:18 UTC+0000
.. 0xfffffa8003866920:iexplore.exe 1592 1596 17 581 2020-04-09 19:10:19 UTC+0000
.. 0xfffffa80017a9060:iexplore.exe 3276 1596 12 377 2020-04-09 19:15:16 UTC+0000
.. 0xfffffa8004007540:iexplore.exe 1760 1596 21 677 2020-04-09 19:12:25 UTC+0000
. 0xfffffa8003c9e910:vmtoolsd.exe 1572 1284 8 154 2020-04-09 19:10:18 UTC+0000
0xfffffa8006278590:csrss.exe 432 420 11 456 2020-04-09 19:10:16 UTC+0000
0xfffffa80079ad5b0:winlogon.exe 484 420 3 112 2020-04-09 19:10:16 UTC+0000
0xfffffa8001753680:thunderbird.ex 424 1380 64 944 2020-04-09 19:14:33 UTC+0000
. 0xfffffa800163a660:helper.exe 2940 424 0 ------ 2020-04-09 19:26:43 UTC+0000
And the only suspicious one was the PID 424 . I’m kidding there were some rabbit holes too (the reptile one but glad i did’nt follow it) but I end up digging the 424 as it also had some weird helper.exe spawned under itself.
Dumping the process using memdump . As the name is thunderbird , it’s an email client by mozilla . The proccess dump actually contained some email addresses and emails.
Identity:email:jarred.a.mclovin@gmail.com
Identity:email:alexthroe376@gmail.com
These were the emails available and grepping to one of the email lead us to this mail.
To: jarred.a.mclovin@gmail.com
Content-Type: multipart/mixed; boundary="000000000000e6890d05a2e08d6f"
--000000000000e6890d05a2e08d6f
Content-Type: multipart/alternative; boundary="000000000000e6890c05a2e08d6d"
--000000000000e6890c05a2e08d6d
Content-Type: text/plain; charset="UTF-8"
Hi Jarred Mclovin,
We are glad you chose us for your CTF Flag needs, and hope you are happy
with our product!
Password: @uVmG4NMus
Sincerely,
ALEX THROE
alex@throe.com <axel@throe.com>
SGALF LLC
DO NO REPLY TO THIS EMAIL
--000000000000e6890c05a2e08d6d
Content-Type: text/html; charset="UTF-8"
Content-Transfer-Encoding: quoted-printable
<div dir=3D"ltr">Hi Jarred Mclovin,<br><br>We are glad you chose us for you=
r CTF Flag needs, and hope you are happy with our product!<div><br></div><d=
iv>Password:=C2=A0@uVmG4NMus<br><br>Sincerely,<br><br>ALEX THROE<br><a href=
=3D"mailto:axel@throe.com" target=3D"_blank">alex@throe.com</a><br>SGALF LL=
C<br><br><br>DO NO REPLY TO THIS EMAIL</div></div>
--000000000000e6890c05a2e08d6d--
--000000000000e6890d05a2e08d6f
Content-Type: application/zip; name="Mclovin.zip"
Content-Disposition: attachment; filename="Mclovin.zip"
Content-Transfer-Encoding: base64
Content-ID: <f_k8t5fbn30>
X-Attachment-Id: f_k8t5fbn30
UEsDBBQACQAIAPSGiFCgeQ8xU4MAAI2bAAARABwATG92aW5JbnZvaWNlLmRvY3hVVAkAA0w6jl63
Q45edXgLAAEE6AMAAAToAwAA5ISKblxOQNsWBnvQmA/Sqm8ph/3ekS3ylL5L55N9fT7tp8yoQrej
ejTqIJNLZernsfzuR4zpwwAWu3SDYKekpG93xkZb6zxPnGY5i/hw7glA0qVL1S2X8lpk6GNy/QqH
aOMd55xJ6mO1uqzD9wN71uilXeKWR8FVJiUDeN1XmsC0N2Hvh/hhWfqq97GLM0+j6ty2I4VmQVIQ
A3F5h4HS/Kp+epagEDHYjIJYqYY8nMM88TgjgapfOkJsdKW6oKuhS1FRrdjrZiwh8yb1zvFiYWUS
eaZ2JHp7/qYMVgigBbdNfd4AvIzKZecxDAGJq+9uPgW2spKHkp6XzXTTTkNL7Fml6GPdMG2UCjzx
bst09JZ0z6TmtikfbzQ0HiY72Gho4h++WemMtS/MxhHPB8zx49lexUEwMLTWalOYkFV7VBg2Kvdi
********************************snipped**************************************
It had a zip attachment and a password with (Password: @uVmG4NMus) . Decoding the base64 we got a zip (password protected). Extracting the zip gave a word file. Extracting the docx file gave a vbaProject.bin . Inspecting the macros with olevba .
olevba 0.55.1 on Python 3.8.1 - http://decalage.info/python/oletools
===============================================================================
FILE: vbaProject.bin
Type: OLE
-------------------------------------------------------------------------------
VBA MACRO ThisDocument.cls
in file: vbaProject.bin - OLE stream: 'VBA/ThisDocument'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Const qeletzpyif = 2
Const jlouvjnmew = 1
Const hgsajszpkq = 0
Private Function jhihworeroqddxunrzx(eatnjvyp As String, snhnkbvor As Long) As String
Dim Tbl, vencfvgarczvufa As String, strTemp, lxpauxezygfacat As String, pwipsogiznsqxl As Long, hykiqmgwmibgmow As Byte
Const cvemyhmtgqsvwbnyzzha As String = "ABCDEFGHIJKLMNOPQRSTUVW" & "XYZ"
Const gqbrepcojoj As Byte = 26
Const wbuccvajxcjjha As Byte = 65 - 1
Const eazcwbvbjqofiqfia As Byte = 97 - 1
strTemp = eatnjvyp
If snhnkbvor < gqbrepcojoj And lngNumber > gqbrepcojoj * -1 Then
vencfvgarczvufa = cvemyhmtgqsvwbnyzzha & cvemyhmtgqsvwbnyzzha & cvemyhmtgqsvwbnyzzha & cvemyhmtgqsvwbnyzzha
Tbl = vencfvgarczvufa
For pwipsogiznsqxl = 1 To Len(strTemp)
If Mid(strTemp, pwipsogiznsqxl, jlouvjnmew) Like xitrlsvziikd("5b612d7a412d") & xitrlsvziikd("5a5d") Then
hykiqmgwmibgmow = Asc(Mid(strTemp, pwipsogiznsqxl, jlouvjnmew))
If Mid(strTemp, pwipsogiznsqxl, jlouvjnmew) = Mid(Tbl, hykiqmgwmibgmow - wbuccvajxcjjha, jlouvjnmew) Then
lxpauxezygfacat = lxpauxezygfacat & Mid(Tbl, hykiqmgwmibgmow - wbuccvajxcjjha + snhnkbvor, jlouvjnmew)
Else
lxpauxezygfacat = lxpauxezygfacat & LCase(Mid(Tbl, hykiqmgwmibgmow - eazcwbvbjqofiqfia + snhnkbvor, jlouvjnmew))
End If
Else
lxpauxezygfacat = lxpauxezygfacat & Mid(strTemp, pwipsogiznsqxl, jlouvjnmew)
End If
Next pwipsogiznsqxl
End If
jhihworeroqddxunrzx = lxpauxezygfacat
End Function
Private Sub bhzktzyjlmcapyvxl()
Dim dcdpcwemxccxonyfp As String
Dim mchyjruygvs As String
Dim ledflensmpxsfkn As String
Dim xynalbyflz As Integer
dcdpcwemxccxonyfp = xitrlsvziikd("206f68") & xitrlsvziikd("6365206b2f20646d63")
mchyjruygvs = xitrlsvziikd("7d2121216c6a336870335f3575316b66334a30785f714a306533655f345f4a6d7b2d") & xitrlsvziikd("584c5556454d")
mchyjruygvs = jhihworeroqddxunrzx(mchyjruygvs, 5)
xynalbyflz = Len(dcdpcwemxccxonyfp)
ledflensmpxsfkn = ""
For pos = xynalbyflz To 1 Step -1
Next_Char = Mid(dcdpcwemxccxonyfp, pos, jlouvjnmew)
ledflensmpxsfkn = ledflensmpxsfkn & Next_Char
Next pos
ledflensmpxsfkn = ledflensmpxsfkn & mchyjruygvs
retVal = Shell(ledflensmpxsfkn, hgsajszpkq)
End Sub
Sub Workbook_Open()
bhzktzyjlmcapyvxl
End Sub
Sub AutoOpen()
bhzktzyjlmcapyvxl
End Sub
Private Function xitrlsvziikd(ByVal ppxscssdlsvg As String) As String
Dim pwfoigdypupp As Long
For pwfoigdypupp = 1 To Len(ppxscssdlsvg) Step 2
xitrlsvziikd = xitrlsvziikd & Chr$(Val("&H" & Mid$(ppxscssdlsvg, pwfoigdypupp, 2)))
Next pwfoigdypupp
End Function
+----------+--------------------+---------------------------------------------+
|Type |Keyword |Description |
+----------+--------------------+---------------------------------------------+
|AutoExec |AutoOpen |Runs when the Word document is opened |
|AutoExec |Workbook_Open |Runs when the Excel Workbook is opened |
|Suspicious|Shell |May run an executable file or a system |
| | |command |
|Suspicious|Chr |May attempt to obfuscate specific strings |
| | |(use option --deobf to deobfuscate) |
|Suspicious|Hex Strings |Hex-encoded strings were detected, may be |
| | |used to obfuscate strings (option --decode to|
| | |see all) |
|Hex String|[a-zA- |5b612d7a412d |
|Hex String|ce k/ dmc |6365206b2f20646d63 |
|Hex String|}!!!lj3hp3_5u1kf3J0x|7d2121216c6a336870335f3575316b66334a30785f714|
| |_qJ0e3e_4_Jm{- |a306533655f345f4a6d7b2d |
|Hex String|XLUVEM |584c5556454d |
+----------+--------------------+---------------------------------------------+
Found a flag like string }!!!lj3hp3_5u1kf3J0x_qJ0e3e_4_Jm{- but was reversed. Reversed it -{mJ_4_e3e0Jq_x0J3fk1u5_3ph3jl!!!} but now from the looks of encryption algorithm it looked like a caesar algo.
And yea it was caesar (18). So the complete flag became
UMDCTF-{uR_4_m3m0Ry_f0R3ns1c5_3xp3rt!!!}.
Kudos to admin for making a great challenge.