Hey there Folks!! Long time no see Huh …

It’s Christmas time and I’m back again with another set of writeups of X-MAS CTF btw we ended 32nd overall and 1st in India :).
Thanks to HTsP for organising this gr8 CTF.
Here are some of the challs.
Cryptography
-
DeFUNct_Ransomware
Forensics
-
Santa’s Forensics 101
-
Santa’s letter
-
A trip to grandma’s house
-
Ddosing the XMAS
MISC
-
Best Friends
DeFUNct Ransomware
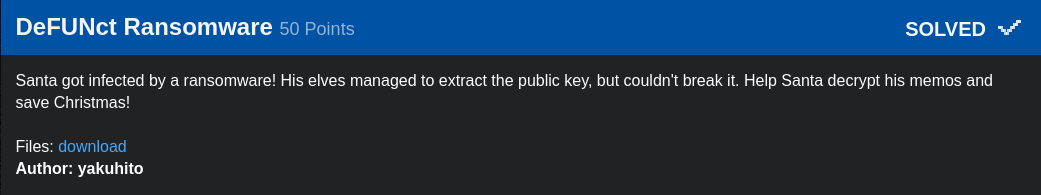
n: 795569463642685540507503580717531982215679866156448758181874864294322245115046429295501396806569726084791213843313411985306755767933614251017259685360119715465741448841742926933764058184678978561438979554324014291467144646477238464467422645352253054043072408503415623126059018449111807300294890437634529289983603557882115343971407081044050231310858245171002149317227947666679143716043142141154344524386085333349328691743473103727587822968025700198172293605188589348169121979328380110985341428872278372426313622759225108517531628814853640680656657769539723198346005032762702856464738405070059566116940640592020837592563966093405895649052241416909627641069000138027201809936286028443581259045590752809132011594533609186039058798304319124598876514669458750171121861029071117458575853963148168447032328126766812085206373608016609150982512467597800331177524543178311636877811255184421602626713179220562081413985985692847372669113031244726086691179028200044542399429299315486513734144695492816493025225952668485937918985944213972980220480476191347009337324778384697829597183756976186825413917475597248616769321954150777672675555280228376126308362907381766363071890237458517881243184612898247096962136202978853341989193954815333784856612689
e: 13337
Public Key (n,e) and Ciphertext has been given to us. So this is a typical RSA challenge.
Factorizing n would give us four factors. ie. p,p,q,q.
p=167945946509710528501147140850136444757936485900233494350920365296618466491038783888459340376962572176658471433672446105042569166930066764067458760954444542315723029727275896055594485064790247910216515269672809063208736956951590237500845779868099616110730494457247861971337900144361732424961936041908032639503
q=167945946509710528501147140850136444757936485900233494350920365296618466491038783888459340376962572176658471433672446105042569166930066764067458760954444542315723029727275896055594485064790247910216515269672809063208736956951590237500845779868099616110730494457247861971337900144361732424961936041908032639503
So n=p*p*q*q. I wrote a short lines of code for this.
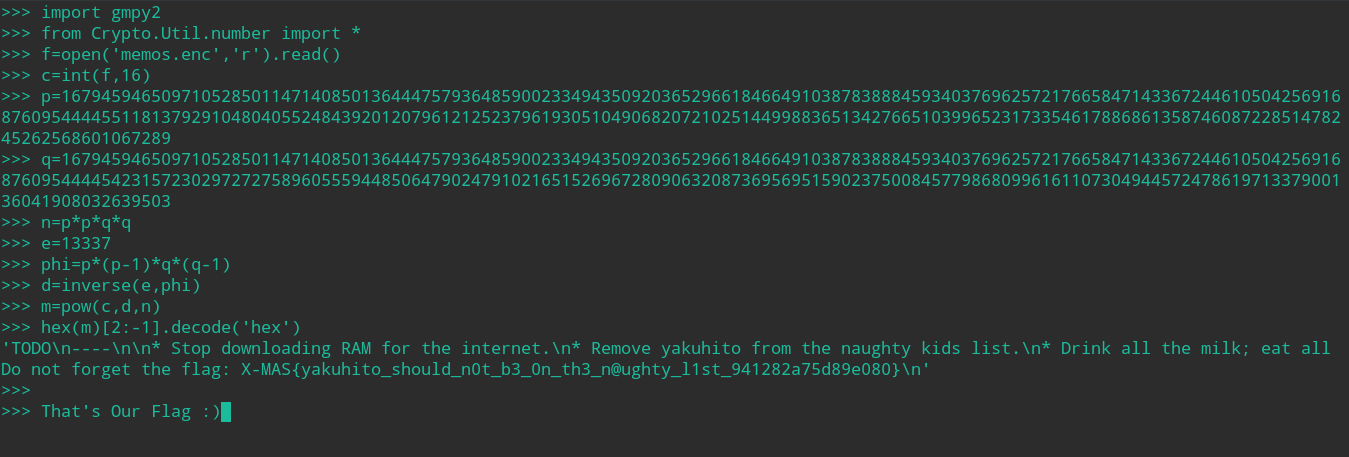
X-MAS{yakuhito_should_n0t_b3_0n_th3_n@ughty_l1st_941282a75d89e080}
Santa’s Forensics 101
A zip has been given to us which contains a png or something that looks like a png :confused:.
file cmd clears that tho.
[badboy17@badboy17-pc Downloads]$ file X-MAS_Flag2.png X-MAS_Flag2.png: Zip archive data, at least v2.0 to extract
Huh a zip again. Extracting it gives the png (a real one :P).

Running strings on it.
[badboy17@badboy17-pc hidden_data_dt]$ strings logo2.png
Gives the flag in the bottom.
X-MAS{W3lc0m3_t0_th3_N0rth_Pol3}.
Santa’s letter
So another Forensics chall with a png.

The Description tho hints us a lot about what to do . But due to our noobism we spent a lot of time on this chall :sweat_smile: .
It seems that Santa may have used some Invisible Ink to write this letter... he is surely playing Hide&Seek.
The invisible Ink part in the desc leads us tohttp://diit.sourceforge.net a steganography tool Digital Invisible Toolkit.
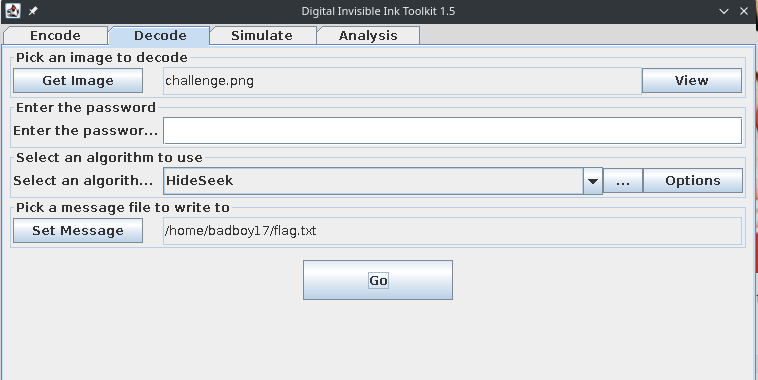
It writes the decoded part to a file . Opening the file gives us the flag.
X-MAS{NOBODY:_SANTA:Hyvää joulua!}
A trip to grandma’s house
A VM forensics chall with a .vdi file. So this chall was super long and it took us three days to figure out and complete the chall.
First we loaded the vdi in the virtual box to see what it was and surprisingly it was a WIN98 image. Boii that’s super Retro.
Booting the VM it asks for the password to login to Thomas’s account.
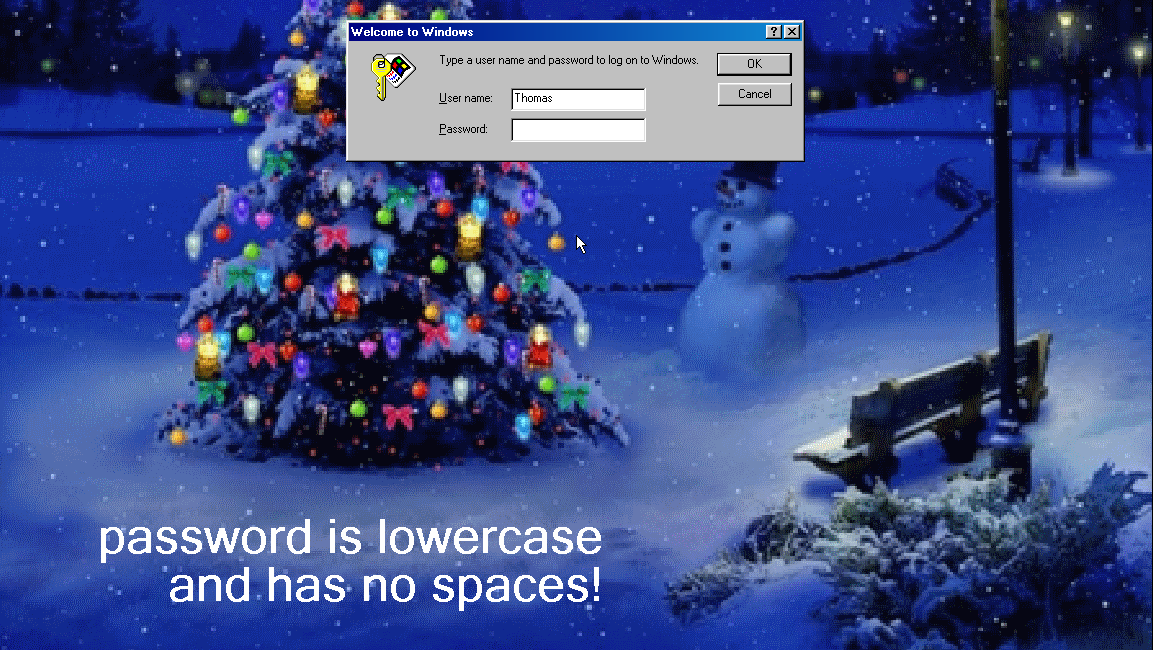
The hint did no good to us as we couldn’t find the password anywhere.
The Second approach I did was to boot in the safe mode and create a new account and copy the files into the new account and changed the Network logon to Windows logon.
Logging in gives this.
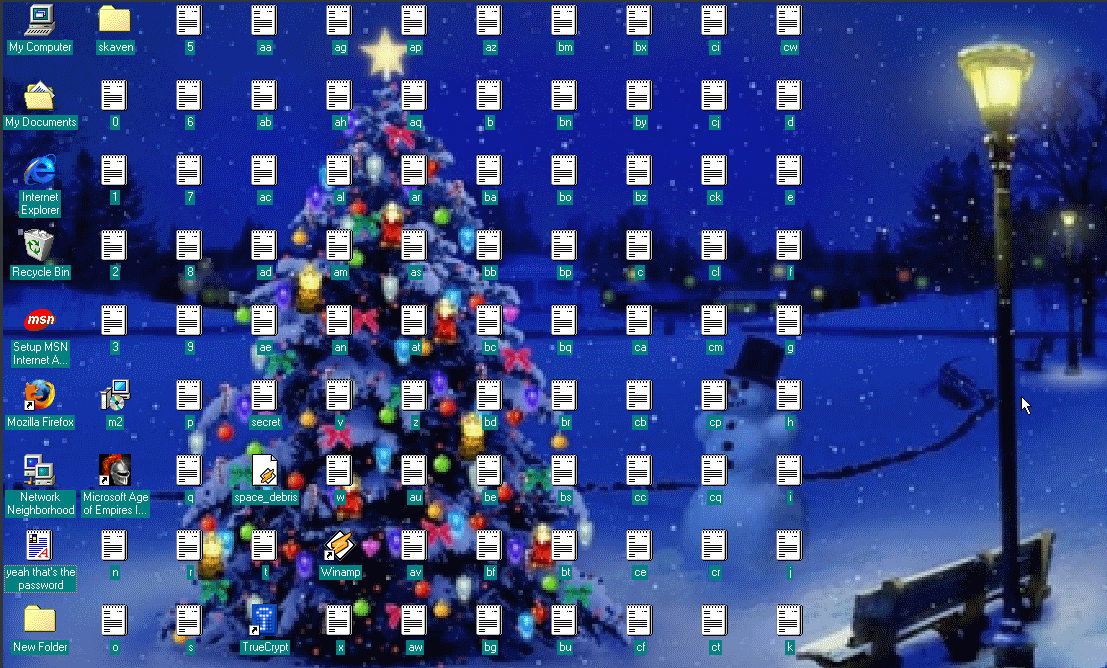
That’s a lot of files Damm. Out of these 3 things caught my eye. Truecrypt secret yeah that's the password. The last file didn’t help much .
Now opening the secret gave us gibberish text. So assuming the fact that it was encrypted with TrueCrypt we still needed the password to decrypt it. The rest of the files in the Desktop actually made something. This was figured by my teammate. It actually spelled out the password for TrueCrypt.

The resolution changed the arrangement of these files. So later a hint was also added .
Hint! Try to login to the desktop without changing the resolution of the VM.
The complete password was mysekritd4tum.
Now that we had everything all it was left to fire the TrueCrypt .
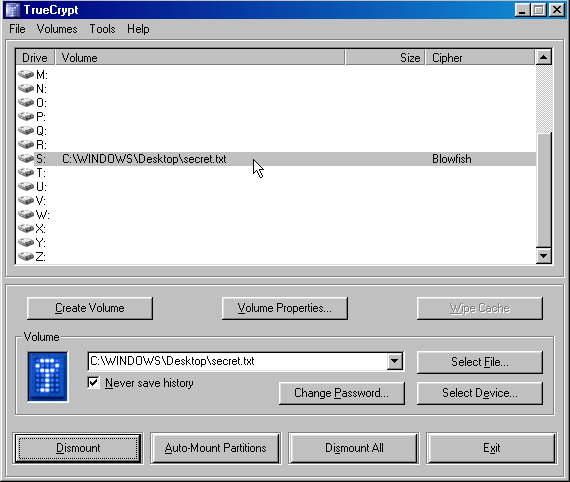
Now the decrypted secret gave us a several other bunch of files.

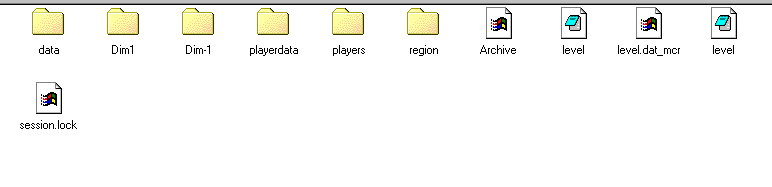
So these files were actually a Minecraft world save. So I transferred the files to my machine.
Now loading the save in the Minecraft gave us the flag. (phewwww.)
Also the flag can be found by a Map renderer.
TOGoS’s Minecraft Map Renderer
[badboy17@badboy17-pc Downloads]$ java -jar TMCMR-2017.09.07b.jar ./mine/region/ -o .


X-MAS{Druaga1_W0uld've_ruN__th1s_0n_4n_SSD}

That’s a super awesome chall and also super awesome teammates. :smile:
DDoSing X-MAS
A file was given to us which was abnormal in someway. Later my teammate figured that it was Xored with (ELF Header)
key=0x24, 0x32, 0x50, 0x52, 0xB2, 0x8C, 0x96
xoring it back again with it gave the Original file. Running file command revealed that it was an ELF binary.
[badboy17@badboy17-pc Downloads]$ file xmas_out xmas_out: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, not stripped
Upon static analysis, it did not gave much of a info. But I do liked the idea of binary :sweat_smile:.
____
__,-~~/~ `---.
_/_,---( , )
__ / < / ) \___
- ------===;;;'====------------------===;;;===----- - -
\/ ~"~"~"~"~"~\~"~)~"/
(_ ( \ ( > \)
\_( _ < >_>'
~ `-i' ::>|--"
I;|.|.|
<|i::|i|`.
(` ^'"`-' ")
BOOM !!! It just ddosed the XMAS.
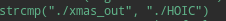
To see what the binary was actually doing behind the scenes I ran it with ltrace . One of the comparison instruction checks arg[0] ie. the name if the binary and it was comparing to HOIC . So I renamed it HOIC.
Again running HOIC with ltrace. The previous check was passed tho but another one came. Now it was opening a file with name KILL_SW1TCH .
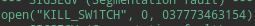
Creating a file with name KILL_SW1TCH with random contents again fired it with ltrace. It now checks the contents of file KILL_SW1TCH .
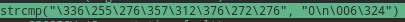
\336\255\276\357\312\376\272\276
These were actually in Bytes form which I figured later. So used python to write in the file.
python2 -c “print ‘\336\255\276\357\312\376\272\276’ “ >
KILL_SW1TCH
A last run gave us the flag.
l0ic . That’s the tool anonymous used for DDOSing. :P
Best Friends
A jpg was given.

Running strings gave this long base encoded string.
R1JTQ0FOUlJFQTNUU0lCV0dJUURNTkpBR0lZQ0FOQlNFQVpHS0lCVUdZUURFWkpBR0lZQ0FOWlRFQTNUSUlCV0dFUURNWkpBR1kyQ0FOWlRFQVpEQUlCV0dZUURNWlJBRzRaQ0FNUlFFQTNUR0lCV01ZUURNWkJBR1kyU0FOWlVFQTNEUUlCV0hFUURNWkpBR1kzU0FNUlFFQTNHTUlCWEdRUURNT0JBR1kyU0FOWlNFQVpEQUlCWEdRUURNT0JBR1lZU0FOVEZFQVpEQUlCV0dJUURNTkpBRzRaU0FOWlVFQVpEQUlCV0dZUURPTVJBR1k0U0FOUlZFQTNHS0lCV0dRUURFTUJBR05RU0FNUlpFQT09PT09PQ==
It was base64 -> base32 -> HEX. Decoding it gave a clear text.
Maybe B.F. stands for something other than best friend :)
Huh. No other clue so as it was a jpg assuming something was hidden with steghide. But there was no password string anywhere. So running stegcracker with rockyou gave us the password in a couple of seconds.
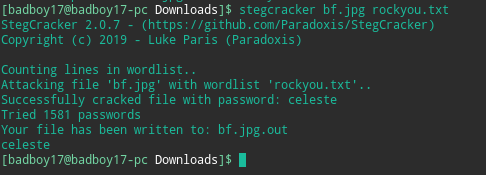
Opening the decoded file :
Maybe increasing the alphabet will make the encryption better
==m65;gVJW1O3>K5^?^YBJag<1i?Yd8RF2n?Sl,'<GaR1F'iB4F*(c$E\V-CA7&hUA79"\AMGqo2Dd*J@:O]
Trying several other decryption methods this turned out to be Base85 .
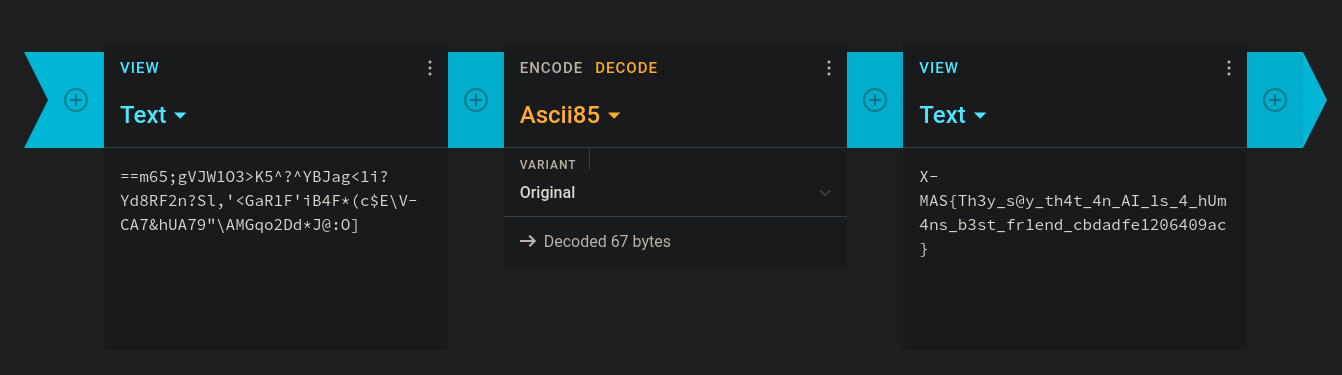
X-MAS{Th3y_s@y_th4t_4n_AI_1s_4_hUm4ns_b3st_fr1end_cbdadfe1206409ac}